Blog
Technical writings, security research findings, and selected company news from our team of experts.
Latest Posts
Minimal LLM-based fuzz harness generator
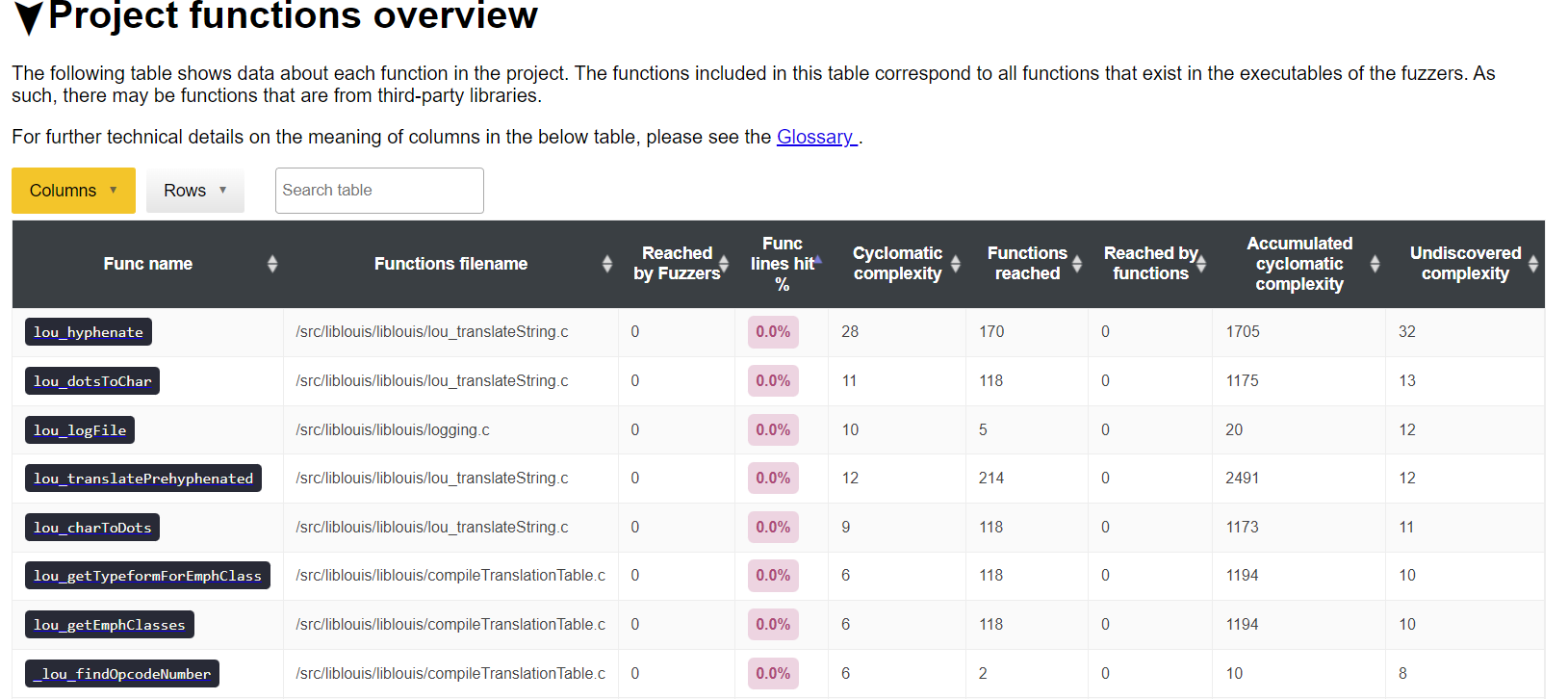
Fuzz Introspector: enabling rapid fuzz introspection tool development

LLVM Fuzzing Audit

Kyverno security audit 2023 findings and report

Structured results for OpenSSF Scorecard - An enabler for custom policies

Crossplane security audit 2023 findings and report

Notation security audit 2023 findings and report
Improving continuous fuzzing of Liblouis

Vitess security security audit 2023 findings and report
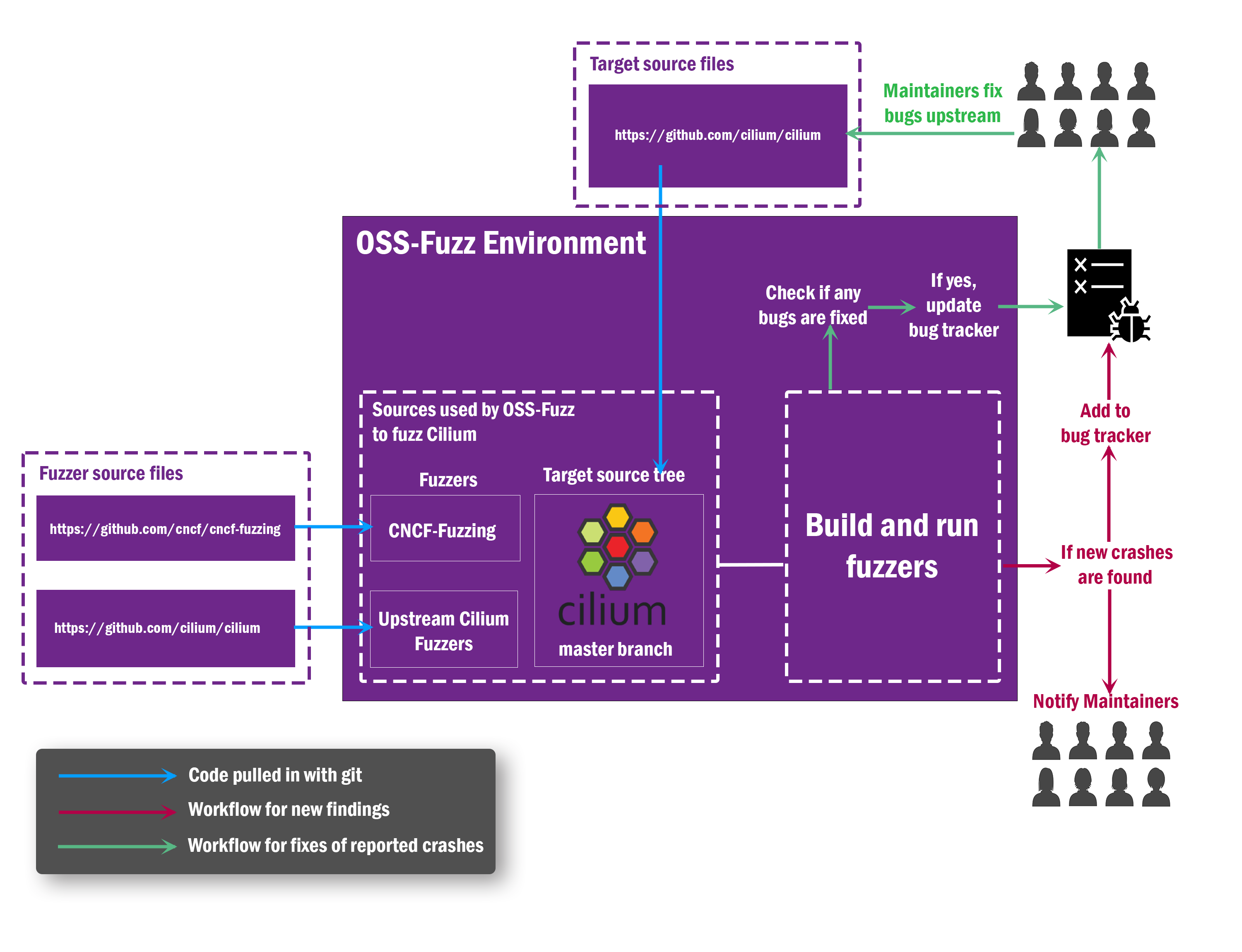
Presenting the findings of Ciliums fuzzing and security audits

Istio service mesh security audit
Jackson-core and Jackson-databind security audit

Ada Logics sets up continuous fuzzing for Cluster API

Argo security audit 2022

KubeEdge holistic security audit engagement

CRI-O holistic security audit engagement

Cloud Native Fuzzing: Istio - 40 crashes and high-severity CVE

Structure-aware Go fuzzing: How to fuzz with complex types
FluxCD Security Audit
Extract text
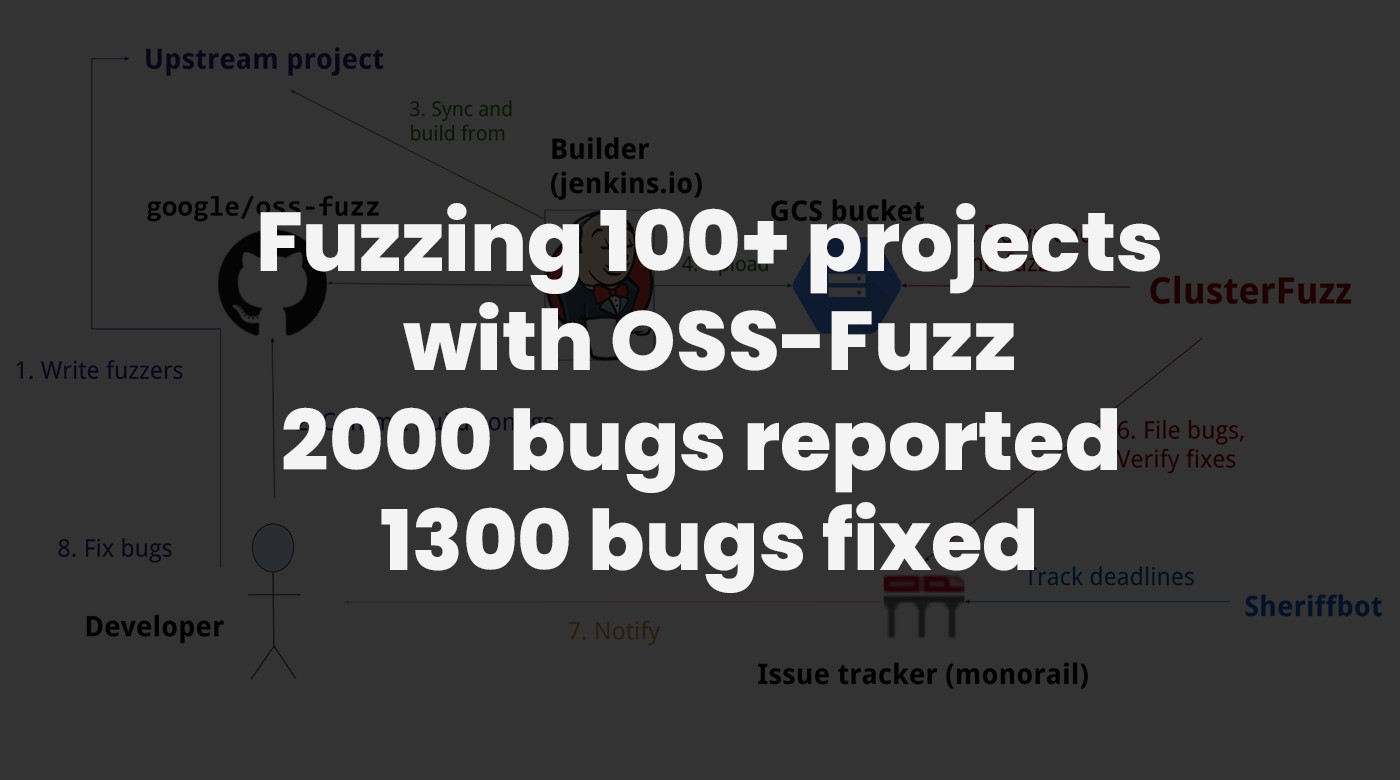
Fuzzing 100+ open source projects with OSS-Fuzz - lessons learned.
In this blog post we will describe our efforts of integrating continuous fuzzing into more than 100 open source projects...

Case study: Oxford University Cyber Security CDT using Ada Logics training for electives
In spring 2021 Ada Logics engaged with Oxford University Centre for Doctoral Training in Cyber Security to deliver three...

Integrating continuous security analysis into Linkerd2-proxy and dependencies
This post covers how Ada Logics integrated continuous security analysis into a state-of-the-art network proxy.

The importance of continuity in fuzzing - CVE-2020-28362
In this blogpost we highlight the importance of continuity in fuzzing based on a recent experience with a security criti...

Securing Open Source: Fuzzing integration, vulnerability analysis and bug fixing of Fluent Bit
Fluent Bit is an open source log processor and part of the Cloud Native Computing Foundation. This fall the Linux Founda...

Getting started with go-fuzz
In this article we will get started with go-fuzz, which is a popular open source fuzzing engine for Go applications. Fuz...
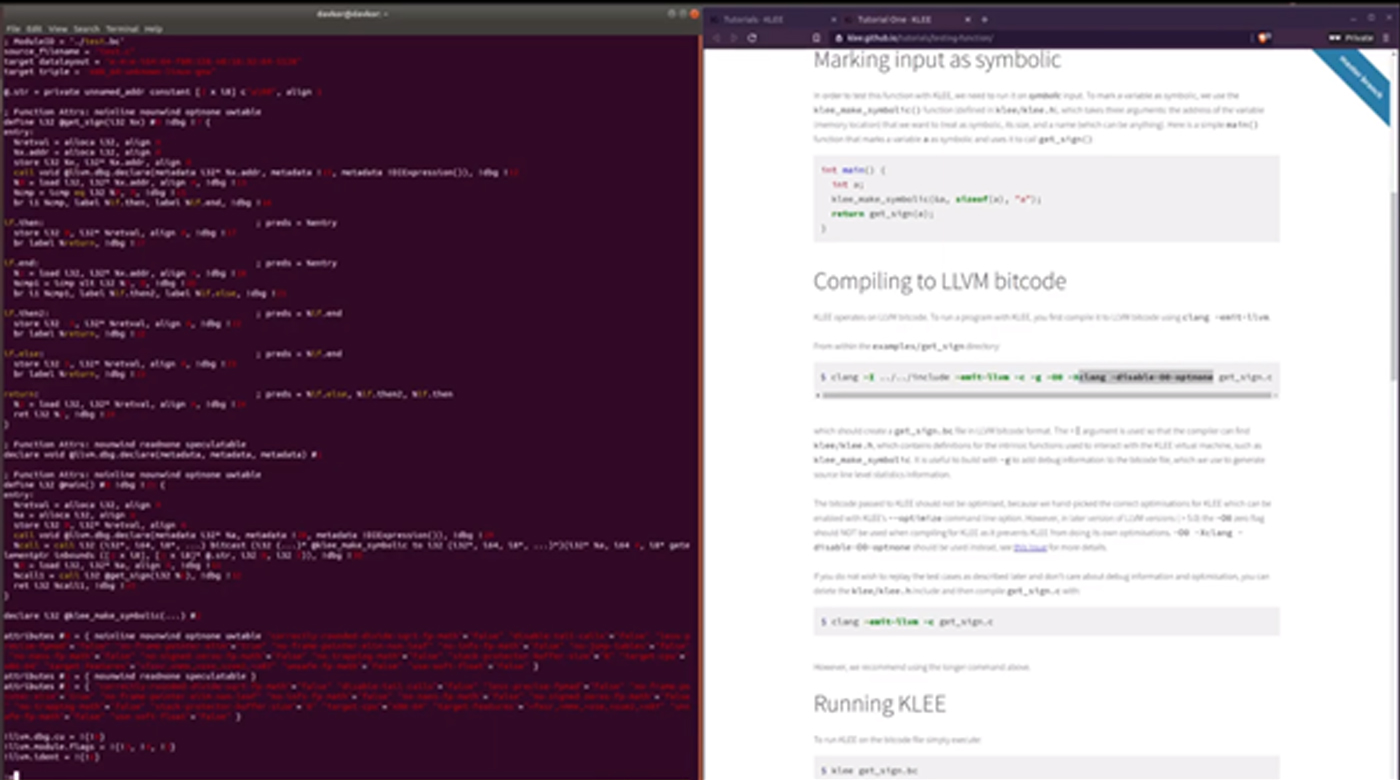
Symbolic execution with KLEE: From installation and introduction to bug-finding in open source software.
In this post we present four videos that cover the KLEE tool. KLEE is a symbolic execution engine that can be used to au...
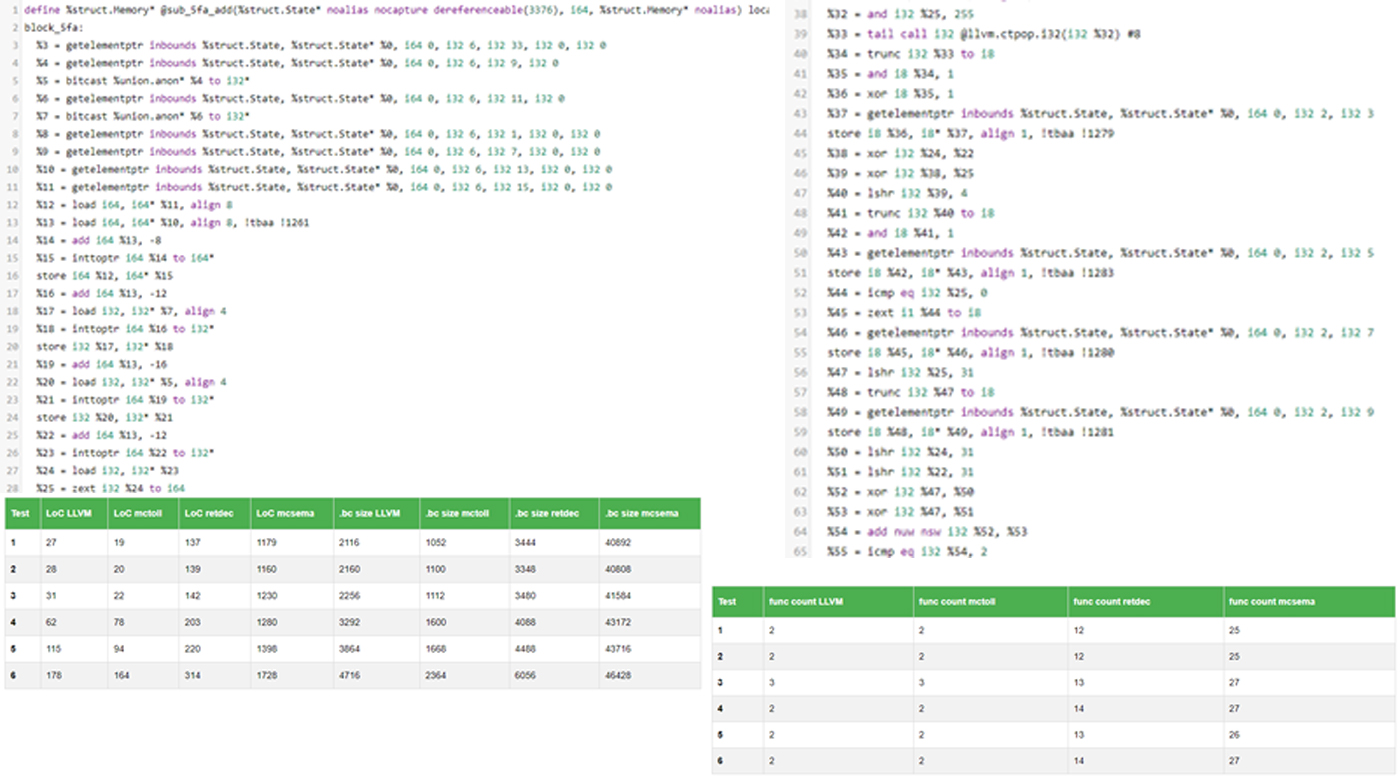
Comparison of the LLVM IR generated by three binary-to-llvm translators
In this blog post we share some brief insights into the code produced three popular binary-to-llvm translators. We do so...
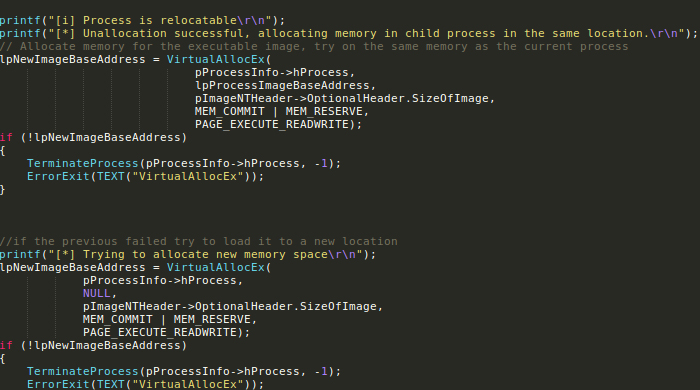
The state of advanced code injections
In the last few years there has been a significant interest in code injection techniques from both attackers and defende...
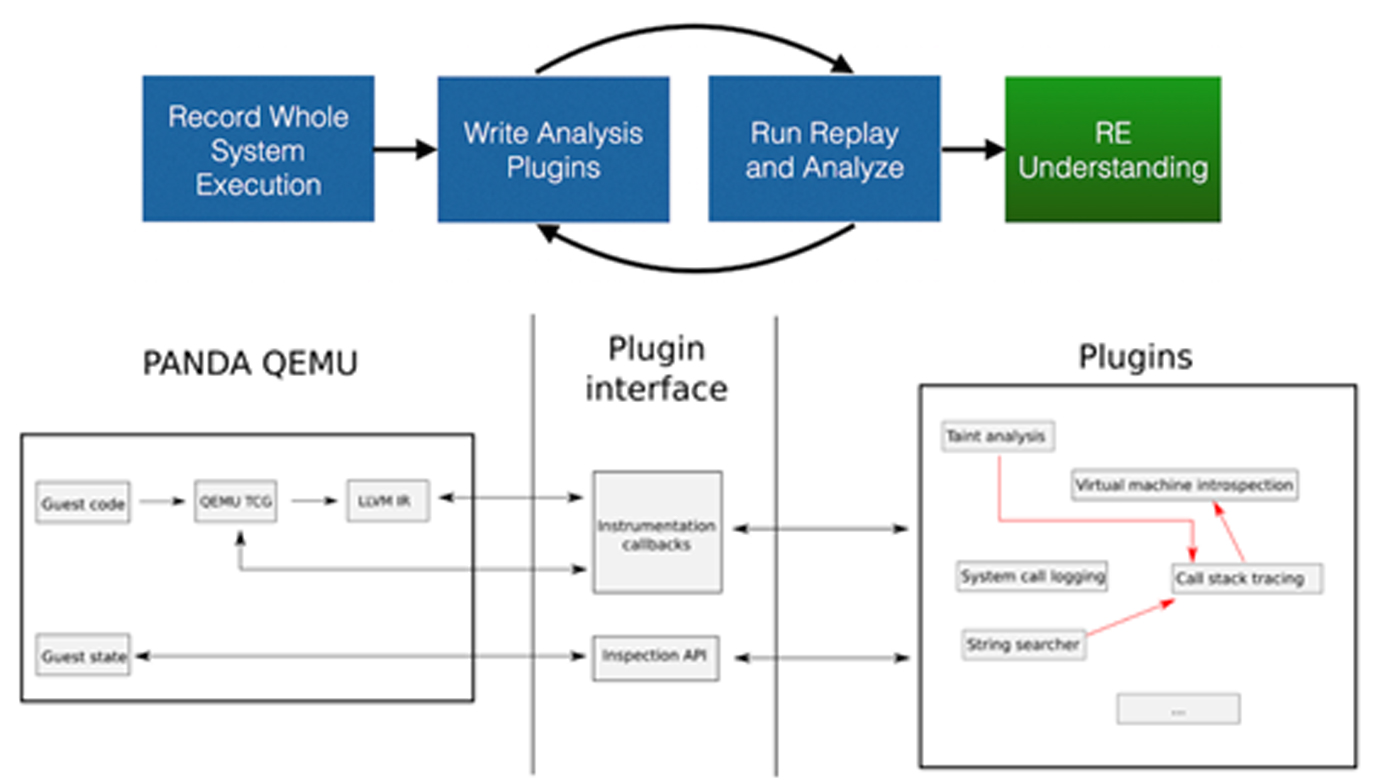
Building a custom malware sandbox with PANDA - Part 1
In the last decade there has been many improvements in fine-grained analysis techniques that focus on automating reverse...

