Presenting the findings of Ciliums fuzzing and security audits
In this blog post we present a fuzzing audit and a security audit of Cilium we recently carried out at Ada Logics.
Fuzzing Audit
The fuzzing audit was done in collaboration with the Cilium maintainers and the CNCF. Fuzzing audits are an important part of establishing modern security practices for CNCF-hosted projects. More than 18 CNCF projects are currently being fuzzed continuously by way of OSS-Fuzz which has found more than 350 bugs across all projects. Read more about the work across the CNCF landscape here: https://www.cncf.io/blog/2022/06/28/improving-security-by-fuzzing-the-cncf-landscape.
The goal of the fuzzing was to improve Ciliums fuzzing suite and make sure the improvements were implemented in a continuous manner. Continuity is a critical element of fuzzing, as we have written about previously. At the time of the audit, Cilium was already integrated into OSS-Fuzz and the work done in this audit was added to this integration to keep the fuzzers running continuously.
Ada Logics wrote 14 fuzzers for the Cilium project. The work committed to the CNCF’s fuzzing repository: https://github.com/cncf/cncf-fuzzing. OSS-Fuzz pulls in the cncf-fuzzing repository at compile time to build the fuzzers. All fuzzing is done against the latest master branch. From a high-level perspective, Ciliums fuzzing architecture looks like this:
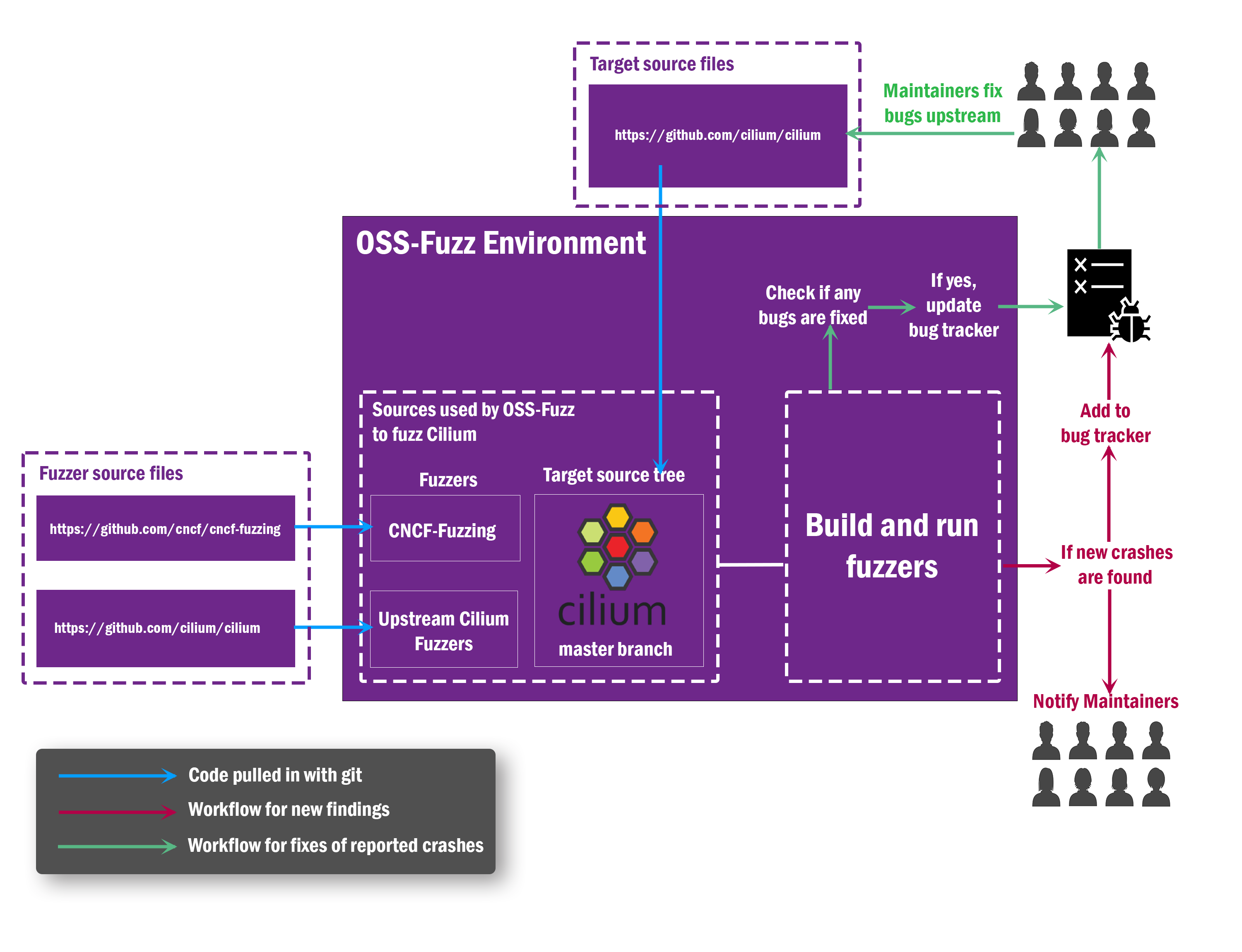
The audit resulted in 8 unique issues being found of the following categories:
- 5 cases of excessive memory allocation.
- 1 index out of range.
- 1 time out.
- 1 nil-dereference.
Security Audit
The security audit was a holistic audit with the following goals:
- Formalise a threat model.
- Perform a manual code audit.
- Improve Ciliums fuzzing suite.
- Carry out a SLSA review.
These 4 goals allowed us to evaluate Ciliums security posture from different angles of modern security practices.
The threat model is meant to be of help for the community as a whole, and we had the following three personas in mind when specifying it:
- Cilium maintainers and security respondents: When a security vulnerability gets reported, root cause analysis requires a contextual awareness, and a threat model assists maintainers achieve that.
- Security professionals who wish to contribute to Ciliums ongoing security posture. This includes the auditors of this particular security audit.
- Non-security-professional Cilium contributors. The threat model provides a perspective for the Cilium community of a non-security background. This community may find bugs of security importance and wish to triage and report these issues.
The manual code audit and fuzzing improvements were done against the insights acquired by the threat model. The manual auditing resulted in 22 issues of informational to medium criticality. The issues of the highest severity were fixed, and the remaining are tracked in this issue: https://github.com/cilium/cilium/issues/23121. The fuzzing work focused on the policy enforcement logic which was identified as a critical part of the Cilium ecosystem. We added 10 fuzzers covering this part and other critical APIs, including 3 for APIs in a critical 3rd-party library.
We would like the CNCF, OSTIF and the Cilium team for the opportunity to contribute to Ciliums security, and we hope that the artifacts published from this audit will inspire other community members to do the same.
The following links cover the work of the two audits:
References
- Fuzzing audit report: https://github.com/cilium/cilium.io/blob/main/Security-Reports/CiliumFuzzingAudit2022.pdf
- Security audit report: https://github.com/cilium/cilium.io/blob/main/Security-Reports/CiliumSecurityAudit2022.pdf
- Ciliums blogpost: https://www.cncf.io/blog/2023/02/13/a-well-secured-project-cilium-security-audits-2022-published/
- OSTIF’s blogpost: https://ostif.org/our-audit-of-cilium-is-complete
- CNCF’s blogpost:https://www.cncf.io/blog/2023/02/13/a-well-secured-project-cilium-security-audits-2022-published/